Operational Technology in CMMC: What’s In Scope and How to Handle It
Introduction
Operational Technology (OT) assets, such as IoT devices, CNC machines, and smart sensors, are becoming integral to modern businesses. However, their inclusion in the scope of CMMC (Cybersecurity Maturity Model Certification) assessments has raised questions and challenges for organizations preparing for compliance.
In this blog, we’ll break down what qualifies as OT, how to determine if it’s in scope, and strategies to handle OT effectively during CMMC assessments. By the end, you’ll have a clear roadmap for managing OT assets and minimizing compliance headaches.
What Is Operational Technology (OT)?
Operational Technology refers to hardware and software systems that manage or monitor industrial equipment, processes, or devices. Examples of OT include:
CNC machines used in manufacturing.
IoT-enabled sensors that monitor temperature or pressure.
Building automation systems like HVAC or security controls.
Unlike traditional IT systems, OT is designed for operational efficiency rather than cybersecurity, which makes it particularly vulnerable to attacks.
Does OT Fall Under CMMC Scope?
The short answer: It depends.
CMMC guidelines categorize OT as a “specialized asset.” Its inclusion in scope depends on whether the OT system:
Connects to the IT Network: OT systems that share the same network as CUI (Controlled Unclassified Information) may fall under scope.
Processes CUI: If an OT system directly handles CUI, it is automatically in scope.
Isolated from IT: OT that is physically or logically isolated may be excluded from scope, but assessors will still require documentation.
Challenges of Managing OT in CMMC Compliance
Complexity: Many OT systems were not designed with cybersecurity in mind.
Documentation Gaps: OT systems are often missing detailed security plans.
Integration Risks: Connecting OT to IT networks introduces vulnerabilities.
Strategies for Managing OT in CMMC Assessments
1. Isolate OT Systems
Physically or logically separate OT systems from your core IT network.
How? Use VLANs, firewalls, or air-gapped networks to segment OT.
Why? Proper segmentation can exclude OT from the scope of your CMMC assessment.
2. Document Everything
Even if an OT asset is out of scope, assessors will require detailed documentation.
Include OT assets in your System Security Plan (SSP).
Provide network diagrams that show how OT is segmented.
Justify exclusions with clear explanations.
3. Implement Security Measures
For OT systems that remain in scope, implement the following:
Access Controls: Limit who can access OT systems.
Monitoring: Use intrusion detection systems to track activity.
Encryption: Safeguard data in transit and at rest.
4. Conduct Mock Assessments
Run a mock assessment to identify potential gaps in your OT security and documentation.
Example: Handling OT in Manufacturing
Scenario: A manufacturing company uses CNC machines connected to the same network as their IT systems.
Before Mitigation | After Mitigation |
OT connected to IT network | OT isolated using VLAN segmentation |
No documentation for CNC machines | CNC machines added to SSP with detailed diagrams |
Risk of OT-based cyberattacks | Implemented firewalls and access controls |
Result: The company successfully excluded their CNC machines from scope, reducing compliance costs by 25%.
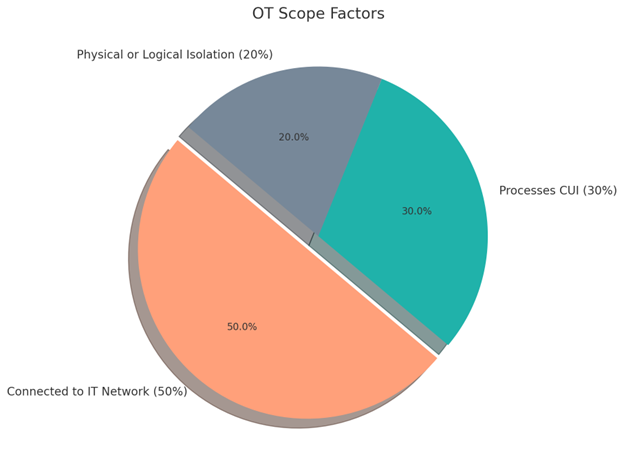
Visual: Pie Chart of OT Scope Factors
(Example Pie Chart)
Connected to IT Network (50%)
Processes CUI (30%)
Physical or Logical Isolation (20%)
Common Mistakes in Managing OT During CMMC Assessments
Assuming “Out of Scope” Means “Ignored”: Even out-of-scope assets must be documented and justified.
Failing to Segment Networks: OT systems on the same network as CUI will always be in scope.
Inadequate Justifications: Provide detailed explanations for exclusions, including diagrams and SSP references.
Conclusion: Managing OT for CMMC Success
Operational Technology adds complexity to CMMC compliance, but with proper planning and documentation, it doesn’t have to be a roadblock. By isolating OT systems, maintaining detailed records, and implementing security measures, businesses can navigate these challenges effectively.
📅 Book Your Free Demo of our Compliance Assessment Tool today and learn how we simplify OT documentation and scope management for CMMC compliance.
